Deep Learning-based Approach for DDoS Attacks Detection and Mitigation in 5G and Beyond Mobile Networks
Introduction
5G networks integrated with IoT devices (here so-called "5G-IoT" networks) uncover several challenges in the security context, due to heterogeneous nodes that demand different network services and present intermittent connection, where traditional security approaches are not always accurate. As a result, several research works have been conducted in the last two decades to optimize security solutions whilst considering 5G-IoT network requirements.
Despite the long-time focus on security by the research community, there's still a lack of works that propose network slicing along with Machine Learning-based approaches, in order to protect 5G-IoT networks from cyber attacks such as Distributed Denial of Service (DDoS).
Network slicing allows the creation of multiple logical instances of the physical network, the so-called "network slices", ensuring strict traffic isolation among them, and tailoring the network resources of each slice to a specific class of applications, by leveraging the concepts of Software Defined Networking (SDN) and Network Function Virtualization (NFV).
Network slicing has the potential to enable the coexistence of a wide range of mobile services in the same network infrastructure. However, enabling 5G-IoT slicing has brought new security requirements and challenges, which have not been addressed neither by 5G standards nor by IoT standards. Indeed, new slicing attack vectors will be added to traditional attacks on 5G-IoT networks, which might jeopardize their adoption.
5G-IoT slicing attacks could exploit users as a weak point, hence violating the slice isolation and deteriorating its performance. The attacks on 5G-IoT slicing can be more powerful, especially if they are combined with internal attacks, which are themselves not easy to detect.
Given the context above, it is of paramount importance having a simple, yet controlled environment that allows users to focus on 5G-IoT cybersecurity applications, that can leverage network slicing to detect and mitigate attacks from malicious users. Such users could be controlled by isolating them to a sinkhole slice, for example.
This demo presents a 5G-IoT platform dedicated to dynamic slicing and mostly cybersecurity applications in a 5G-IoT context. The platform counts with a Web application that allows users to manage slices and select the proper slicing policy, basing on the users' behavior. The Web application also allows developers to easily add new policies that would focus on different kinds of attacks. IoT devices are managed by a parallel platform called BeC3 [3], which is integrated to the local 5G network.
Description of the Hardware/Software Resources
The base Hardware/Software resources deployed in this demo are presented in the figure below.
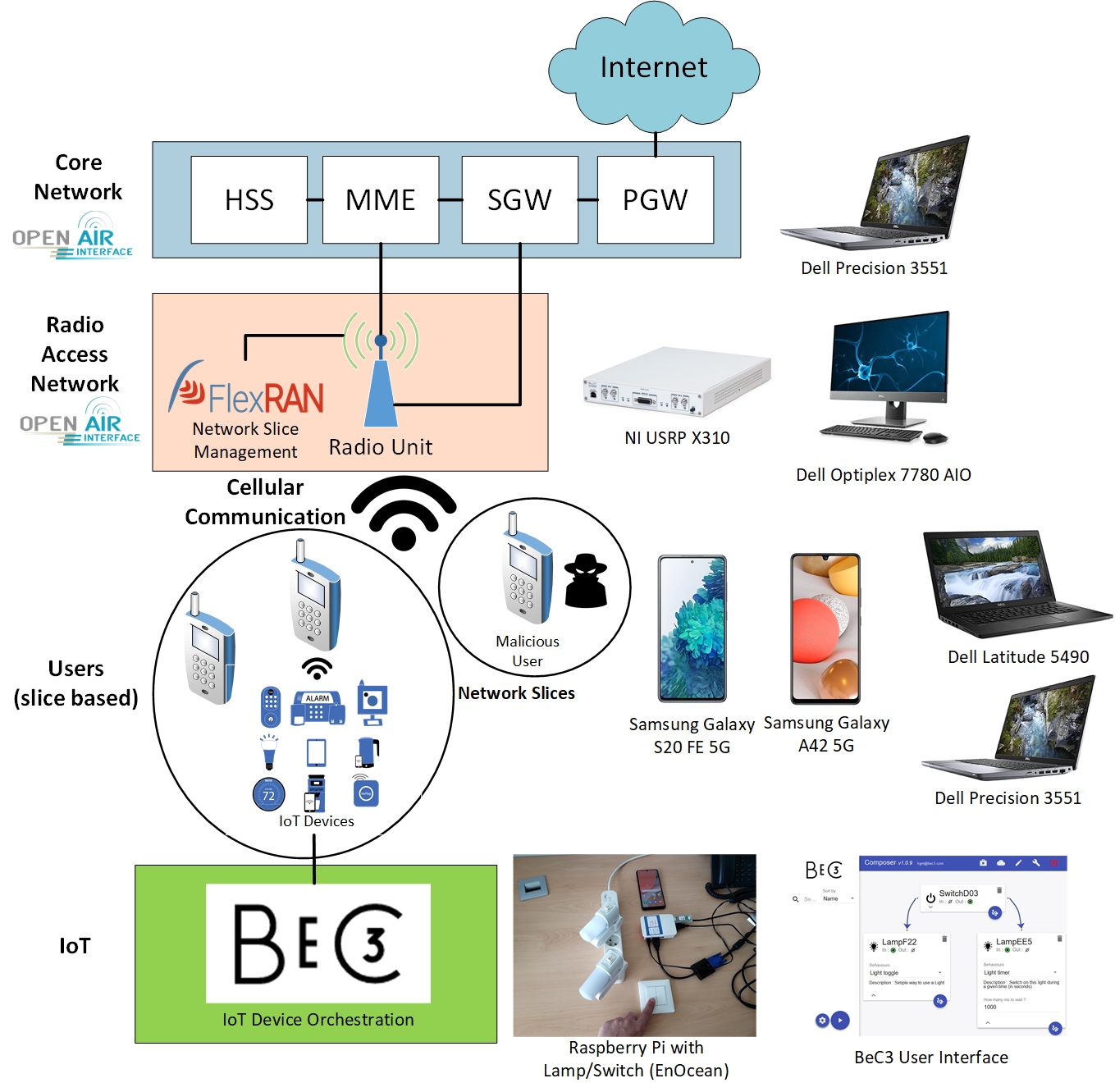
To emulate the cellular network elements (i.e., the Core Network - CN, and the Radio Access Network - RAN), we use OpenAirInterface (OAI) [1]. OAI is an open-source software suite developed by Eurecom to support mobile telecommunication systems like 4G and 5G. OAI counts today with a wide development community that constantly contributes to expand OAI, in order to make it as close as possible to a commercial cellular network provider. In this way, new network functions and solutions could be easily tested and validated with smaller costs.
To deploy the CN elements, composed in this scenario by the Home Subscriber Server (HSS), the Mobility Management Entity (MME), the Serving Gateway (SGW) and the Package Gateway (PGW), we use a Dell Precision 3551 laptop which provides access to the Internet. On the other hand, for the RAN we use a Dell Optiplex 7780 AIO Desktop PC, which is in turn connected to a USRP X310 card [4]. The USRP card is responsible to emulate the radio unit, thus creating the communication interface between the RAN and the cellular users, here represented by two different Commercial Off-the-Shelf (COTS) smartphone models: The Samsung Galaxy S20 FE 5G and the Samsung Galaxy A42 5G.
For the proposed cybersecurity context, we use FlexRAN [2] to manage network slices in real time, in order to protect benign from malicious users (e.g., by isolating the latter in sinkhole slices with few or no ressources, this way mitigating their action). To deploy the attacks in our demo, we use two laptops: one Dell Latitude 5490 and one Dell Precision 3551. The laptops are connected to separate Wi-Fi hotspots created by the smartphones, which in turn are connected to the cellular network. To emulate the attacks, two different tools are used: Mausezahn [6] and Metasploit [7].
Finally, in order to orchestrate the IoT devices we use BeC3, which allows us to instantiate real and/or virtual IoT devices and the interaction between them. Bec3 acts as an intermediate point between IoT devices from different vendors, creating a common communication protocol that allows a simplified integration. The IoT infrastructure can be defined and deployed in Bec3 through a simple Web interface, accessible from any machine. In order to integrate the IoT devices with the 5G network, we leverage the 5G users' Wi-Fi hotspot interface. In our demo scenario, the IoT devices are represented by two sets of lamps/smart power plugs and one button switch (EnOcean standard), as well as a Raspberry Pi that does a local controlling of these devices.
Slicing Web Application
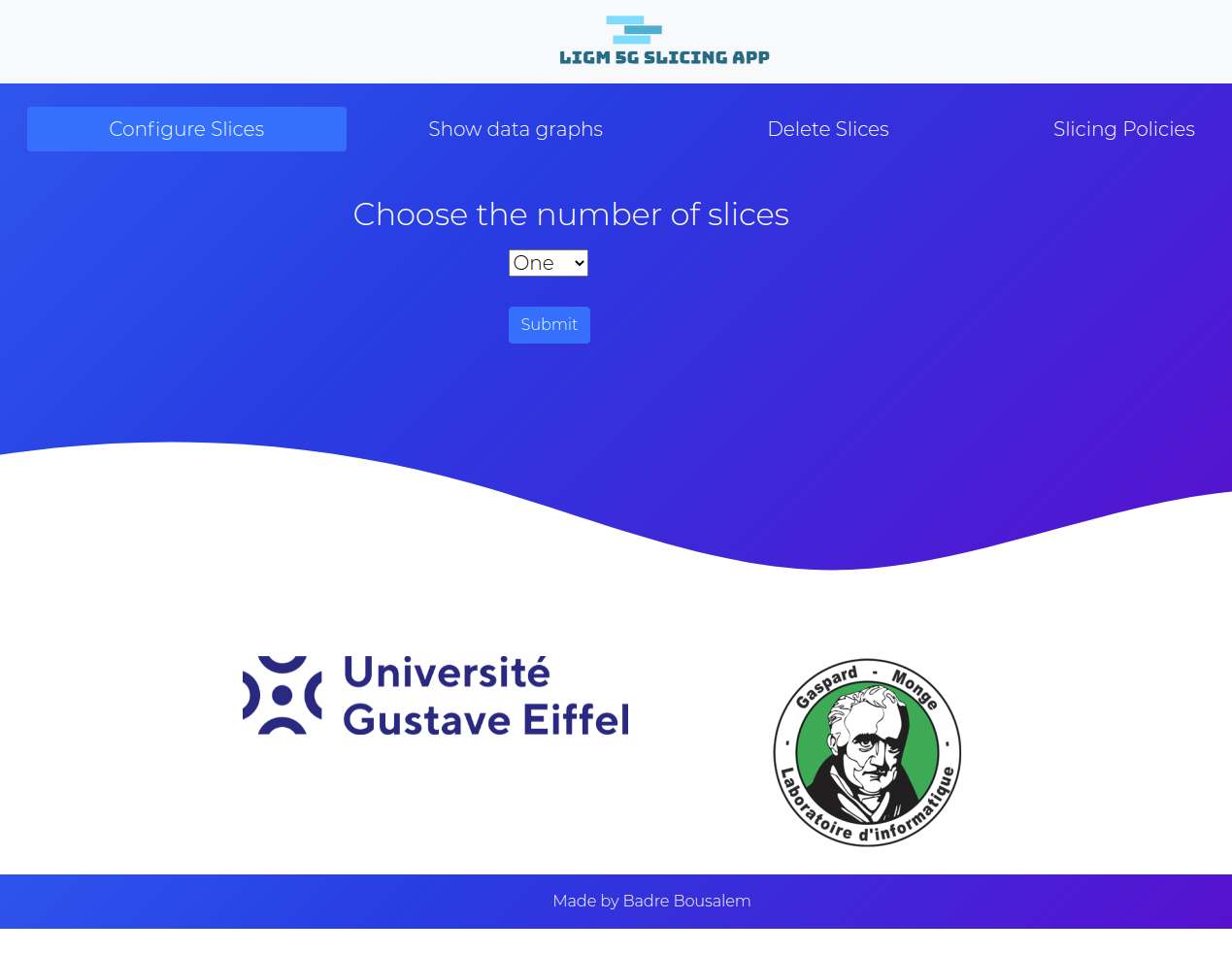
In order to simplify slice management in real time with the FlexRAN agent, as well as the deployment of different slicing policies, a Web-based user interface was developed and integrated to the 5G-IoT platform. This web interface also allows users to create/delete network slices manually, as can be seen in the figure below.
The slicing policies have a dedicated tab, where the user can configure and trigger the proper policy according to the network demand. The figure below shows one of the policies developed in our lab, whose steps will be described and presented in a video below. This policy is based on Deep Learning techniques that were inspired by the Lucid framework [5] and aims to detect DDoS attack events.
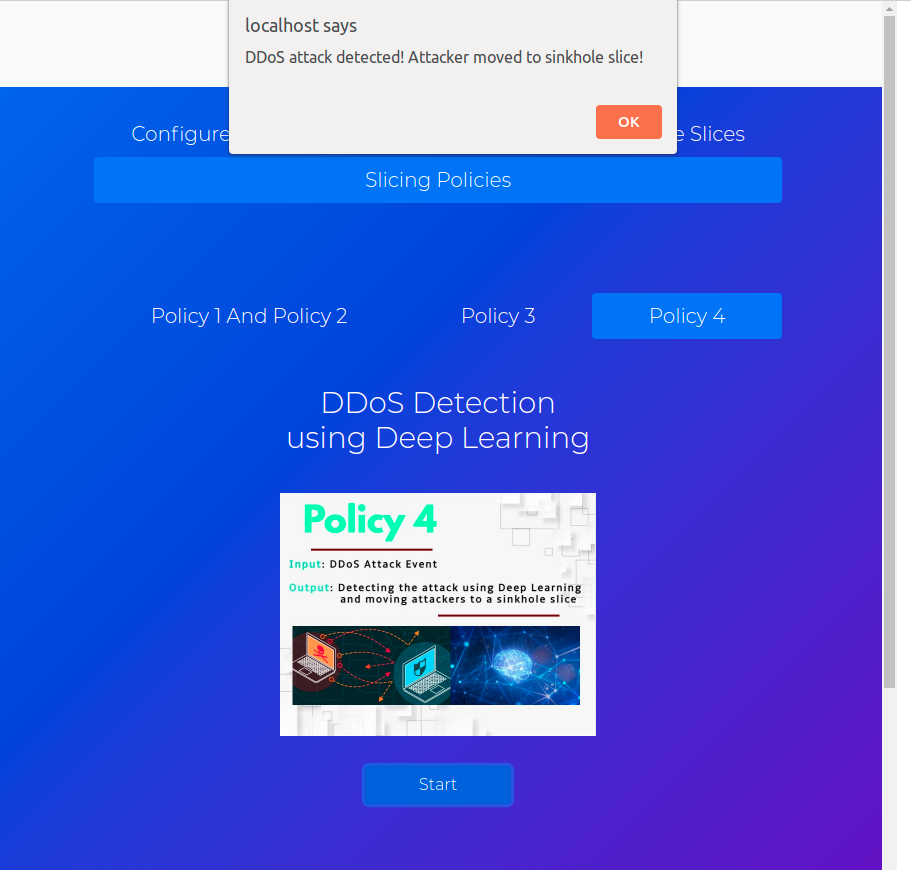
The learning module, which was designed by using Convolutional Neural Networks (CNNs), continuously observes the malicious users' behavior, in order to detect and predict their actions with more accuracy in the future. Once an attack event is detected, a sinkhole slice is created to which the malicious users are moved.
Demo Video
REFERENCES
[1] OpenAirInterface, online, https://openairinterface.org/
[2] FlexRAN, online, https://mosaic5g.io/flexran/
[3] Sylvain Cherrier, Ismail Salhi, Yacine Ghamri-Doudane, Stéphane Lohier, Philippe Valembois. BeC3: Behaviour Crowd Centric Composition for IoT applications. Springer Mobile Networks and Applications (MONET) Journal, 2014, 19 (1), pp.18-32. https://hal.archives-ouvertes.fr/hal-01378059
[4] National Instruments, online, https://ni.com, https://ettus.com
[5] R. Doriguzzi-Corin, S. Millar, S. Scott-Hayward, J. Martínez-del-Rincón and D. Siracusa, "Lucid: A Practical, Lightweight Deep Learning Solution for DDoS Attack Detection," in IEEE Transactions on Network and Service Management, vol. 17, no. 2, pp. 876-889, June 2020, doi: 10.1109/TNSM.2020.2971776.
[6] Mausezahn, online, http://netsniff-ng.org/
[7] Metasploit, online, https://www.metasploit.com/
[8] B. Bousalem, V. F. Silva, R. Langar, and S. Cher- rier, "Deep Learning-based Approach for DDoS At- tacks Detection and Mitigation in 5G and Beyond Mobile Networks," in Proc. of IEEE International Conference on Network Softwarization (IEEE NetSoft), Demo Paper, June 2022.
